Interface specifications HM-MR chain authorization
This page describes the messages for the backchannel interface between an Herkenningsmakelaar (HM) (broker) and a Machtigingenregister (MR) (authorization information provider).
Elektronische Toegangsdiensten only supports chains with one intermediary:
User_G (user) > Intermediary_A > ServiceConsumer_B.
The Intermediary_A registers a mandate for User_G at MR1 and the ServiceConsumer_B registers a mandate for Intermediary_A at MR2. MR2 has no user-interaction, therefore the User_A has to select ServiceConsumer_B (including appropriate MR2) at MR1 in order to proceed with chain authorization flow. MR1 can use discovery-services (of all MR2) during mandate registration of Intermediary_A or during user authorization flow.
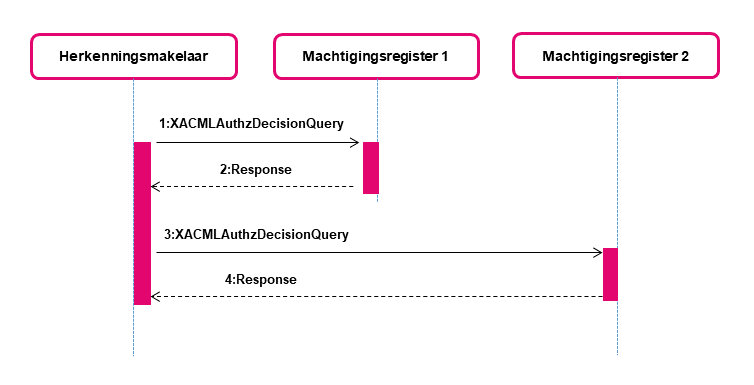
MR1 receives a HM-MR request
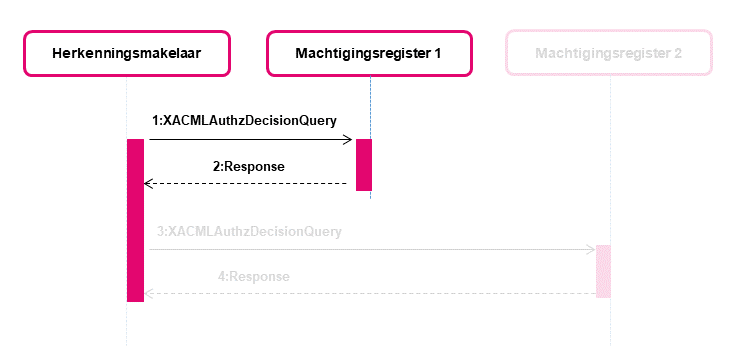
After receiving the AD-response, the HM forwards User_G via a HM-MR request to MR1. At that point the MR1 will decide together with the User_G if the request will be a standard or 'authorisation-chain' request. In the case of a chain authorisation the the rules for processing will be slightly different than described in Interface specifications HM-MR. Below only the differences to default HM-MR process rules are described per 'subsection'.
Rules for processing request
Subsection | Differences to default HM-MR process rules |
|---|---|
A receiving MR MUST provide an Assertion: |
|
Rules for processing response
Subsection | Differences to default HM-MR process rules |
|---|---|
A receiving HM: |
|
Examples
Example of Response with Obligations
<xacml-context:Response xmlns:xacml-context="urn:oasis:names:tc:xacml:2.0:context:schema:os">
<xacml-context:Result>
<xacml-context:Decision>Permit</xacml-context:Decision>
<xacml-context:Status>
<xacml-context:StatusCode Value="urn:oasis:names:tc:xacml:1.0:status:ok" />
</xacml-context:Status>
<xacml-policy:Obligations>
<xacml-policy:Obligation ObligationId="urn:etoegang:core:RequireConfirmationFromNextMR" FulfillOn="Permit">
<xacml-policy:AttributeAssignment DataType="http://www.w3.org/2001/XMLSchema#string"
AttributeId="urn:etoegang:core:AuthorizationRegistryID">urn:nl:eherkenning:MR:99999900000001:entities:0017
</xacml-policy:AttributeAssignment>
</xacml-policy:Obligation>
</xacml-policy:Obligations>
</xacml-context:Result>
</xacml-context:Response>HM requests MR2 via SOAP interface
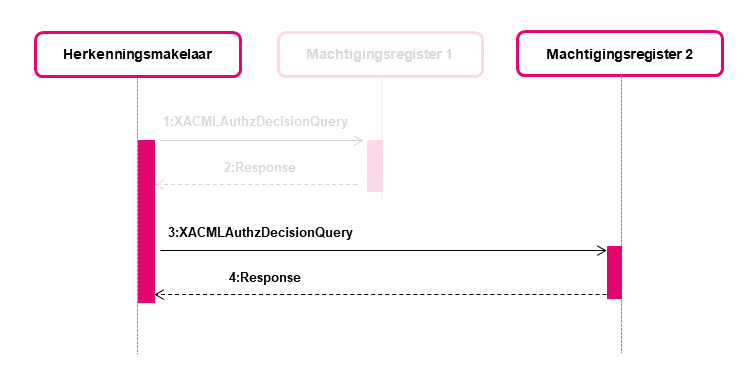
This query and response resemble the XACMLAuthzDecisionQuery and Response as described in Interface specifications HM-MR, but differs on the following aspects.
Rules for processing request
Subsection | Differences to default HM-MR process rules |
|---|---|
A requesting HM: |
|
Rules for processing request
Subsection | Differences to default HM-MR process rules |
|---|---|
A receiving MR MUST provide an Assertion: |
|
ServiceUUID and Portal Request
A ServiceUUID (value) in the specifications always represents a ServiceInstanceUUID, which is a DV-specific ServiceInstance of a ServiceDefinition. A ServiceDefinition is identified using a ServiceUUID which is can be referred to as a ServiceDefinitionUUID. Mandates are registered on a ServiceDefinition (not a DV-specific ServiceInstance). Therefor MR1 and MR2 have to check on valid mandates by looking up the ServiceDefinition belonging to the requested ServiceInstance.
MR2 is not allowed to extent or reduce the ServiceInstance-list in MR1 assertion. Even more, MR2 will Deny the request if Intermediairy_A does not have a valid mandate for all of the services in this list. To prevent such a deny, MR1 should be very carefull composing the ServiceInstance-list and only add ServiceInstance's in the response for which the Intermediary has a mandate (from ServiceConsumer_B) at MR2. MR1 can use DiscoveryService for this purpose.
Intermediate.CompanyName
is the name of the Intermediate Company that MR2 uses when ServiceConsumer_B is registering or managing mandates for this intermediate. The Intermediate CompanyName is either the registered official name or trade name (KvK: statutaire naam of handelsnaam). CompanyName has a value of urn:etoegang:1.13:attribute-Intermediate:CompanyName. MR2 always has to return the Intermediate CompanyName. Except when the ServiceProvider does not have an encryption certifiate in the ServiceCatalog for this service. Because attributes always need to be encrypted.
